Connecting to a server using OpenSSL
What is OpenSSL?
OpenSSL is an open source cryptographic tool used to secure communication over computer networks.
Using the terminal we are going to connect to cyberstorm.mu which is acting as the server here, using OpenSSL from our VM which is the client.
The command to be used : openssl s_client cyberstorm.mu:443
Note: s_client means we are in client mode and 443 is the port through which we are connecting to cyberstorm.mu
 |
| Result from the command |
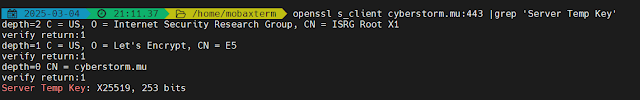
But what we are most interested in all of the output given is the 'Server Temp Key' field. This field will help us identify whether this connection is using a post-quantum secure connection.
As we are only focusing on the 'Server Temp Key' field, we are going to use 'grep' command with a pipe so we can search that field from the given output.
The command to be used :
openssl s_client cyberstorm.mu:443 | grep 'Server Temp Key'
Using the above picture, we can see in the 'Server Temp Key' field that the key agreement is X25519.
However X25519 is not post-quantum secured which means there can be a possible risk of a quantum computer attack.
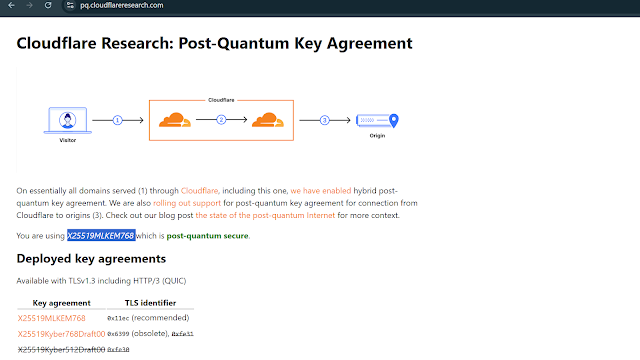
Post-quantum key agreements for X25519 is valid when it is concatenated with MLKEM768 and others.
Connecting to https://pq.cloudflareresearch.com/ which is the server from our browser (Client), we can see that the key agreement it is using is X25519MLKEM768 which is post-quantum secure.

Comments
Post a Comment